
A data breach broker is selling the allegedly stolen user records for twenty-six companies on a hacker forum, BleepingComputer has learned.
When threat actors and hacking groups breach a company and steal their user databases, they commonly work with data breach brokers who market and sell the data for them. Brokers will then create posts on hacker forums and dark web marketplaces to market the stolen data.
Last Friday, a data broker began selling the combined total of 368.8 million stolen user records for twenty-six companies on a hacker forum.
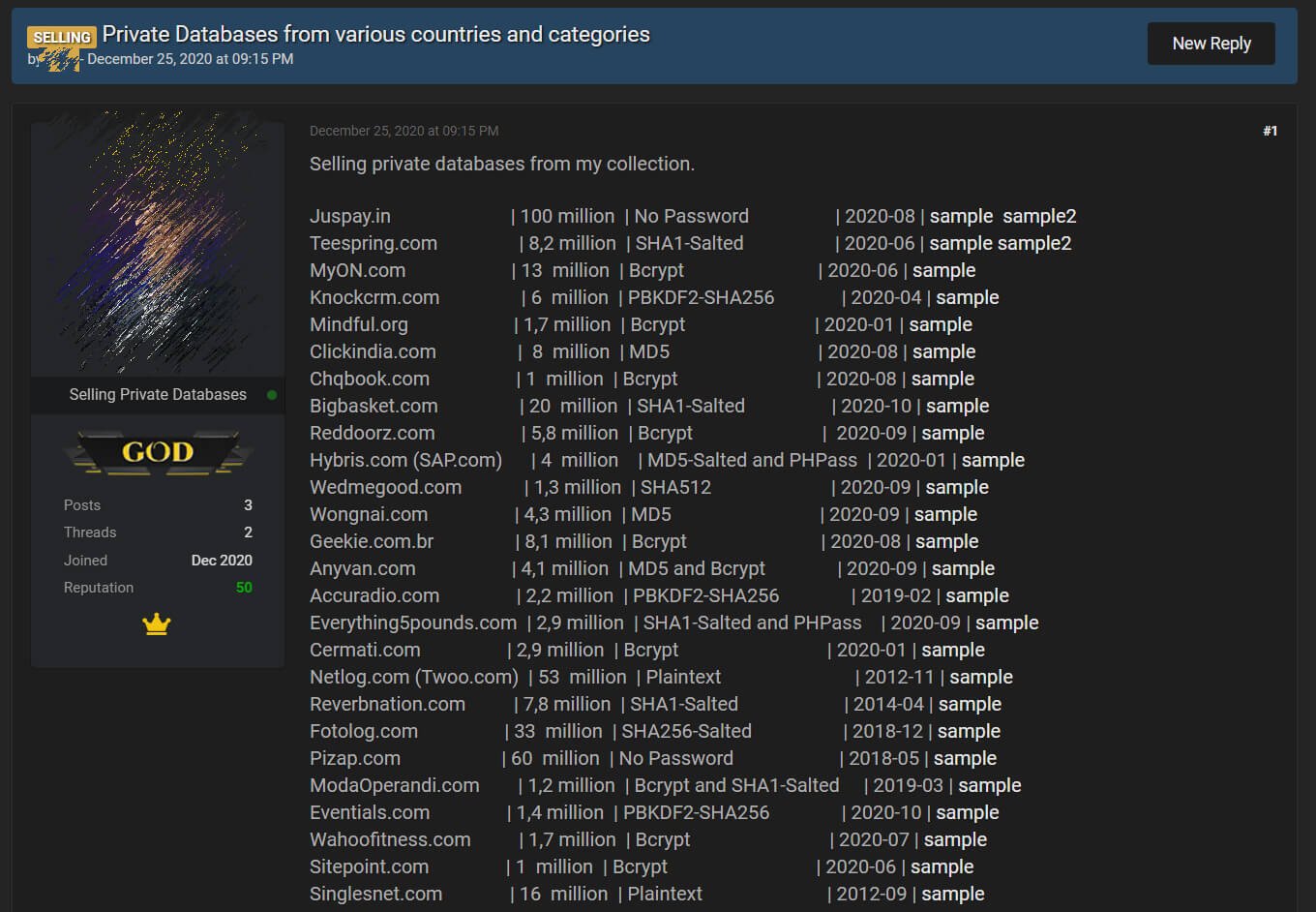
Of these twenty-six companies, only eight are new alleged data breaches that have not been previously disclosed. These seven companies are Teespring.com, MyON.com, Chqbook.com, Anyvan.com, Eventials.com, Wahoofitness.com, Sitepoint.com, and ClickIndia.com.
In a conversation with the data broker, BleepingComputer was told that Teespring is being sold for $3,800-$4,000, MyON for $2,800, and Chqbook for $1,800. The broker has not decided on pricing for the other databases.
The full list of companies whose alleged data is being sold, including the number of user records and whether they were previously disclosed, is listed below.
| Company | User Records | Known? |
| Teespring.com | 8.2 million | Yes |
| MyON.com | 13 million | No |
| Chqbook.com | 1 million | No |
| Anyvan.com | 4.1 million | No |
| Eventials.com | 1.4 million | No |
| Wahoofitness.com | 1.7 million | No |
| Sitepoint.com | 1 million | Yes |
| Clickindia.com | 8 million | No |
| Juspay.in | 100 million | Yes |
| Knockcrm.com | 6 million | Yes |
| Mindful.org | 1.7 million | Yes |
| Bigbasket.com | 20 million | Yes |
| Reddoorz.com | 5.8 million | Yes |
| Hybris.com (SAP.com) | 4 million | SAP client data |
| Wedmegood.com | 1.3 million | Yes |
| Wongnai.com | 4.3 million | Yes |
| Geekie.com.br | 8.1 million | Yes |
| Accuradio.com | 2.2 million | Yes |
| Everything5pounds.com | 2.9 million | Yes |
| Cermati.com | 2.9 million | Yes |
| Netlog.com (Twoo.com) | 53 million | Yes |
| Reverbnation.com | 7.8 million | Yes |
| Fotolog.com | 33 million | Yes |
| Pizap.com | 60 million | Yes |
| ModaOperandi.com | 1.2 million | Yes |
| Singlesnet.com | 16 million | Yes |
Responses from companies
After learning about this forum post, BleepingComputer reached out to the companies that have not been previously disclosed in the past.
MyON confirmed that their systems was breached but stated that student's private data was not exposed.
"In July 2020 we were made aware of a bad actor trying to sell portions of our data on the dark web. We immediately began investigating to shut down any continued threats to our data or the data of our customers. We were then able to confirm that according to federal and state privacy laws, no confidential student or customer data was compromised, and this incident did not rise to the level of an actual breach of student private data."
"We are committed to the protection of the privacy of our user’s and customer’s data and have instituted supplemental protections in addition to our standard information security measures. Additional information about those efforts is outlined in our information Security Overview and our online Privacy Hub at https://www.renaissance.com/privacy/," MyON told BleepingComputer via email.
From the samples seen of the MyON data breach, the exposed information consisted of login names, BCrypt hashed passwords, and names.
In an email to BleepingComputer, Chqbook.com claims that they were not breached.
"There has been no data breach and no information belonging to our customers has been compromised. Data security is a key priority area for us and we conduct periodic security audits to ensure the safety of our customers’ information," Chqbook told BleepingComputer.
BleepingComputer has emailed some of the users listed in the Chqbook sample to confirm if the data belongs to them.
BleepingComputer contacted TeeSpring on December 27th, after finding out about the breach, and was told they were investigating it. After further attempts to contact them about the breach, they refused to reply to our emails.
We learned later that they had already disclosed the data breach notification on December 1st, but included a noindex HTML tag that prevented the advisory from being indexed by search engines.
We can't be sure if the TeeSpring stolen data was used maliciously but we have already received reports of phishing emails reaching Teespring users' mailboxes.
What should users of these sites do?
Other than MyON and Chqbook's statements, it has not been confirmed if the other six companies have suffered a data breach.
Historically, sold data breaches like this tend to be legitimate, and companies soon disclose them after the new becomes public.
For now, if you have an account at any of the sites listed above, it is strongly suggested that you change your password to a strong and unique one used only at that site.
If the same password has been used at other sites, change your password to a unique one there as well.
BleepingComputer recommends using a password manager to keep track of strong and unique passwords at sites you have accounts.
Update 1/22/20: Added further information about TeeSpring data breach notification.


Comments
dogsofhellfire2600 - 3 years ago
Thanks for the update. Keep it coming.
L1g3rZ3r0 - 3 years ago
The only company website I'm familiar with is RevervNation. I used to use it.
nkiko - 3 years ago
So basically 3/4 is from Shiny Hunters lmao. Teespring is known for a long time they hacked it like 3 months ago or more
geercom - 3 years ago
'Nice update, Lawrence. These kinds of sales are common on the dark web. Many go unreported, lengthening the duration of the credentials' usefulness to black hat hackers.
CometJo - 3 years ago
Yeah, I found this article because I got spam today at an email alias that I only ever used for TeeSpring.
I bet their data has already been sold to someone.
CometJo - 3 years ago
Also, see this article from Teespring -- they know about the breach:
https://community.teespring.com/blog/security-incident-june-2020/
Lawrence Abrams - 3 years ago
Thanks we updated the article.