Product & Solutions
Resources
FREE TOOLS
Website Security Assessment SSL Certificate Checker Domain Expiry Checker HELP AND SUPPORT
Help Center Developer HubCompany
Network equipment manufacturer giant Cisco confirmed on 11 August 2022 that their corporate network got breached by the Yanluowang ransomware group on 24 May 2022.
It was due to a phishing attack that targeted one of their employee’s Google accounts in which the corporate credentials were stored.
Also, they mentioned that the hackers could only find and steal the non-sensitive data from the folder in that employee’s account.
The initial access to the Cisco VPN was obtained by gaining access to one of the Cisco employees’ personal Google accounts.
The password syncing was enabled in the browser due to which the corporate credentials were stored.
Post obtaining access to the employees’ accounts, the attacker bypassed Multi-Factor Authentication (MFA) using a variety of techniques, which includes vishing (voice phishing) and MFA fatigue. MFA fatigue is the process of sending many push notifications to the target’s device until the user accepts, either unintentionally or to quiet the repeated push notifications.
In this scenario, the employee had been receiving multiple calls for a number of days, in which they spoke in English in multiple international accents and dialects – which were convinced to be from support organizations trusted by the user.
Post obtaining access, the attacker enrolled another device for MFA and was able to get authenticated to the Cisco VPN.
After that, the attacker tried to perform privilege escalation to administrative accounts which triggered the alert to Cisco Security Incident Response Team (CSIRT). The hackers had managed to load several tools including remote access tools like TeamViewer and LogMeIn, offensive security tools such as Cobalt Strike, PowerSploit, Mimi Katz, and Impacket plus a set of persistence mechanisms and backdoor accounts.
After gaining access to the system, the bad actors executed operations to maintain access, minimize the forensic activities, and to escalate the access level.
They began to enumerate using the common built-in Windows utilities to gain more information about the user and group configuration of the system, hostname, and further details.
Post gaining VPN access, the bad actors used compromised accounts for logging on to numerous other systems. And then moving to the Citrix environment (cloud-based, VPN-less solution which helps to access the intranet, mobile, SaaS, and virtual applications) to compromise a set of Citrix servers and obtain access to domain controllers. And then, they dumped the NTDS using “ntdsutil.exe” consistent with:
powershell ntdsutil.exe 'ac i ntds' 'ifm' 'create full c:\users\public' q q
The attacker was seen using machine accounts for the purposes of lateral movement and privileged authentication inside the environment post gaining access to credential databases.
Also, the attacker created an administrative user account named “z” using the in-built “net.exe” commands and moved the same to the local Administrator groups using the commands:
C:\Windows\system32\net user z Lh199211* /add
C:\Windows\system32\net localgroup administrators z /add
This account was then used to attempt to enumerate the directory services environment and obtain additional credentials using utilities such as adfind or secretsdump. Also, the attacker extracted registry information, including SAM database on the compromised host using:
reg save hklm\system system
reg save hklm\sam sam
reg save HKLM\security sec
With this, on some hosts, the attacker deployed MiniDump to dump LSASS (Local Security Authority Subsystem Service) by:
tasklist | findstr lsass
rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump [LSASS_PID] C:\windows\temp\lsass.dmp full
The evidence of intrusion conducted on the systems was removed by deleting the local Administrator account and “wevtutil.exe” utility was used to clear the event logs generated.
wevtutil.exe el
wevtutil.exe cl [LOGNAME]
net user z /delete
And they even modified the firewall configuration of the host to enable RDP (Remote Desktop Protocol) access to the systems. Also, they used the RDP and Citrix services to move files between the devices in the network itself by using:
netsh advfirewall firewall set rule group=remote desktop new enable=Yes
Additionally, remote access tools such as TeamViewer and LogMein were installed and executed using:
C:\Windows\System32\msiexec.exe /i C:\Users\[USERNAME]\Pictures\LogMeIn.msi
The bad actor leveraged Windows login bypass techniques to maintain the ability to access the devices in the environment with administrative privileges. And they often relied on PSEXESVC.exe to remotely add Registry values by using:
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\narrator.exe /v Debugger /t REG_SZ /d C:\windows\system32\cmd.exe /f
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe /v Debugger /t REG_SZ /d C:\windows\system32\cmd.exe /f
With this, the attacker leveraged the windows accessibility features “narrator.exe” and “sethc.exe” in the Windows login screen to spawn root level command prompt to gain complete control over the systems.
Interestingly, according to the report from Cisco Talos, the bad actors added the keys as mentioned but did not interact with the system. This might be to remain a persistence mechanism to use when their access is revoked.
The initial payload was a simple backdoor that took commands from the C2 (Command-and-Control) server and executed them on the end system via the Windows Command Processor. Also, there was a “DELETE_SELF” command which removes the backdoor from the system upon an incident.
And the “WIPE” command was also there which cleared the previous command from the memory.
To retrieve the commands, HTTP GET requests were made to the C2 server using:
/bot/cmd.php?botid=%.8x
Also, the malware communicated with the C2 server through HTTP GET requests using:
/bot/gate.php?botid=%.8x
After the first request from the infected system, the C2 server responded with SHA256 hash, and it was observed making additional requests every 10 seconds.
A file named “bdata.in” was also created in the malware’s working directory which had values from the volume serial number of the infected system. Also, the backdoor was observed running in
C:\users\public\win\cmd.exe.
On the systems from which they were operating, the attacker has regularly seen staging tools in directory locations under the public user profile. According to the investigation of C2 infrastructure by the Cisco team, they were able to conclude that the C2 server was set up with the sole purpose of executing this attack.
CSIRT and Talos stated, “we are responding to the event, and we have not identified any evidence suggesting that the attacker gained access to critical internal systems, such as those related to product development, code signing, etc.” And “The threat actor was successfully removed from the environment and displayed persistence, repeatedly attempting to regain access in the weeks following the attack; however, these attempts were unsuccessful.”
The above-mentioned TTPs (Tactics, Techniques, and Procedures) are listed below based on the different phases of the attack in which they occurred.
ATT&CK Technique: Phishing (T1566)
ATT&CK Technique: Valid Accounts (T1078)
ATT&CK Technique: System Services: Service Execution (T1569.002)
ATT&CK Technique: Create Account: Local Account (T1136.001)
ATT&CK Technique: Account Manipulation: Device Registration (T1098.005)
ATT&CK Technique: Event Triggered Execution: Image File Execution Options Injection (T1546.012)
ATT&CK Technique: Indicator Removal on Host (T1070)
ATT&CK Technique: Indicator Removal on Host: Clear Windows Event Logs (T1070.001)
ATT&CK Technique: Masquerading: Match Legitimate Name or Location (T1036.005)
ATT&CK Technique: Impair Defenses: Disable or Modify System Firewall (T1562.004)
ATT&CK Technique: Modify Registry (T1112)
ATT&CK Technique: OS Credential Dumping: LSASS Memory (T1003.001)
ATT&CK Technique: OS Credential Dumping: Security Account Manager (T1003.002)
ATT&CK Technique: OS Credential Dumping: NTDS (T1003.003)
ATT&CK Technique: Multi-Factor Authentication Request Generation (T1621)
ATT&CK Technique: Remote Services (T1021)
ATT&CK Technique: Query Registry (T1012)
ATT&CK Technique: Application Layer Protocol: Web Protocols (T1071.001)
ATT&CK Technique: Remote Access Software (T1219)
ATT&CK Technique: Encrypted Channel: Asymmetric Cryptography (T1573.002)
ATT&CK Technique: Proxy: Multi-hop Proxy (T1090.003)
ATT&CK Technique: Exfiltration Over Alternative Protocol (T1048)
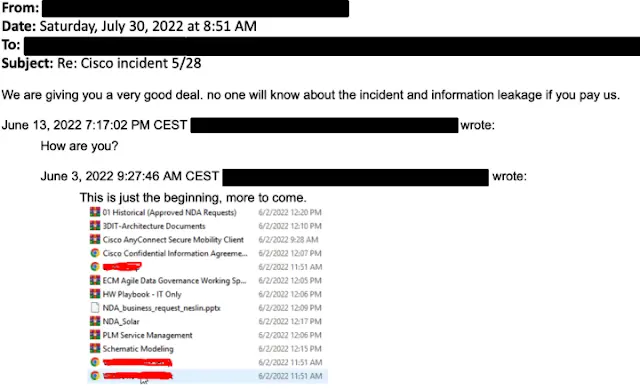 Yanluowang email to Cisco
Yanluowang email to Cisco